Seamless LDAP/Active Directory Integration
-
"It’s great to hear we are forward thinking with our approach unlike our competitors who just want to use this for SSO."
Darren Chalmers-Stevens, former VP Technical Services, in email to myself.
Although the LDAP integration within IPSecurityCenter became a political hot potato within the company and never saw the full potential that it offered a few within the business, such as Darren, were both technically and commercially aware enough to see my vision and how it would provide more than the competitors.Where as the competition such as Milestone only used Active Directory for SSO, my concept was to use it within the whole tool kit of IPSecurityCenter and for example treat LDAP objects just as we did any other object. This would provide a unified view within the product of all locations, contacts and other resources in the LDAP repository.
By concentrating on LDAP and not simply one implementation of it, Active Directory, this would have allowed interoperability with for example Windows NT, which I knew one customer still had in place, as well as IBM Tivoli which I also knew one of the customers, who was also a reference site, used instead of Active Directory.
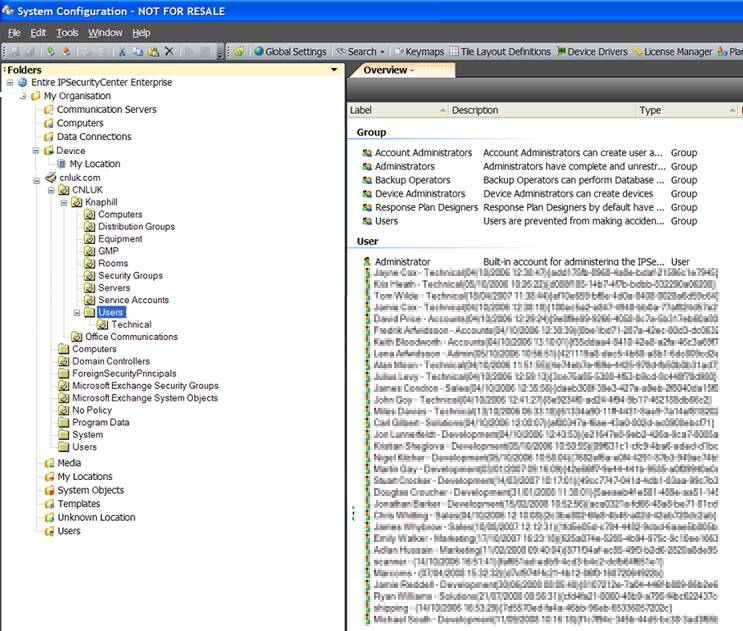
Unlike competitors that only allowed on connection the prototype services that I developed allowed multiple connections to multiple LDAP providers. In addition the LDAP organisational unit structure was exposed to the user by grafting the nodes into the existing IPSecurityCenter organisational structure. The grafted nodes could be placed anywhere within the IPSecurityCenter system, and the root of the grafted nodes could be any node within the LDAP structure. This allowed the implementation to present the Active Directory within IPSecurityCenter as a totally different domain model from the AD domain if they wished.
The potential to be able to connect to both AD for authentication and at the same time ERP/CRM packages such as SAP and to be able to directly access Human Resource information, for example for people who did not even work in the company such as suppliers and customers, was enormous if that step had been to take allow a broader situational awareness.
Using the strategy and adapter design patterns simplified the code, and presented the LDAP objects as if they were native IPSecurityCenter objects. In this way events and therefore triggers could be placed on ldap objects, so for example if a user is disabled or added in LDAP/AD then workflow could be initiated to lock down systems, produce reports or anything else. Appearing as native objects also allowed LDAP person and group objects to be used seamlessly within the existing IPSecurityCenter security model. Very little work had to be performed on the existing code base to instantly open up a much bigger feature set than anyone else had released.
Footnote: To date IPSecurityCenter still has not realised the full potential of the feature and it has become a simple tick in the box "Me too" feature, which is a shame as one developer after a "Show and Tell" stated:
"It's too good an integration"
A great opportunity lost when all the hard work had already been done.